When was the last time you evaluated your customer service security? Your support team handles sensitive customer data every day. One security breach could cost millions in damages and permanently damage customer trust. Yet many organizations still rely on basic security measures that leave them vulnerable to increasingly sophisticated cyber threats.
Why Customer Service Security Matters Now More Than Ever
Support teams are prime targets for cybercriminals because they:
– Handle sensitive customer data daily
– Process financial and personal information
– Operate across multiple channels and devices
– Work remotely with varying security controls
– Face sophisticated social engineering attacks
Let’s explore 10 proven ways to strengthen your customer service security and protect sensitive data.
1. Implement Role-Based Access Control (RBAC)
Role-based access control is your first line of defense against unauthorized data access. By limiting each team member’s permissions to only what they need, you dramatically reduce security risks.
Implementation Checklist:
– [ ] Define clear roles (Admin, Manager, Agent)
– [ ] Map required permissions for each role
– [ ] Remove unnecessary access rights
– [ ] Regularly audit access levels
– [ ] Document role definitions and permissions
Pro Tip: Review and update role permissions quarterly to ensure they align with current job responsibilities.
2. Enable Two-Factor Authentication (2FA)
Two-factor authentication adds an essential security layer beyond passwords. When implemented correctly, 2FA can prevent 99.9% of automated attacks.
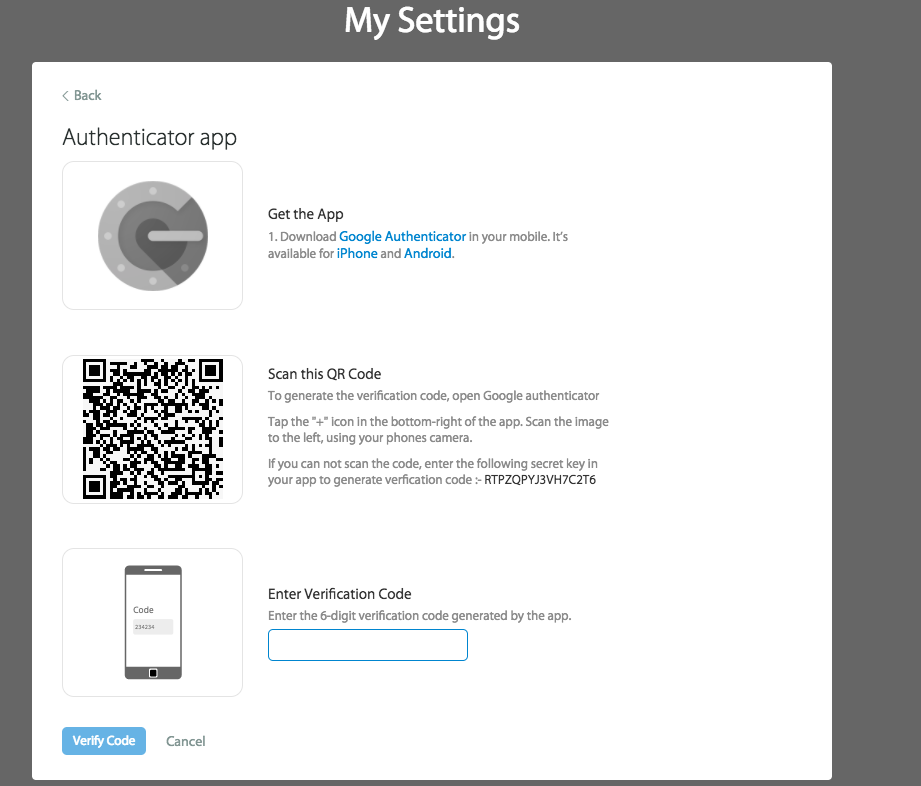
Key Implementation Steps:
– Make 2FA mandatory for all support staff
– Use authenticator apps instead of SMS
– Enforce regular authentication renewal
– Monitor failed authentication attempts
– Provide backup authentication methods
3. Encrypt All Customer Communications
Data encryption isn’t optional anymore – it’s essential for protecting customer information in transit and at rest.
Security Best Practices:
– Use 256-bit SSL encryption for all communications
– Implement end-to-end encryption for sensitive data
– Regularly update encryption protocols
– Monitor encryption certificate validity
– Train agents on secure communication practices
4. Establish IP Range Restrictions
Limiting access to your support system to specific IP ranges adds another crucial security layer.
Implementation Guidelines:
– Define allowed IP ranges for office and remote work
– Implement VPN requirements for remote access
– Monitor and log access attempts from unauthorized IPs
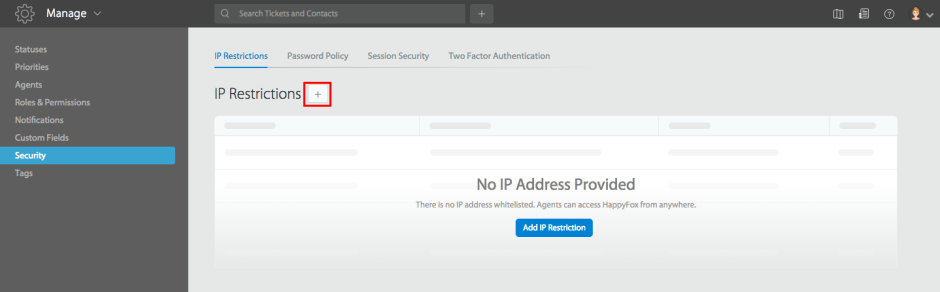
– Regularly review and update IP allowlists
– Create emergency access protocols
Learn more: IP Restrictions in HappyFox Help Desk
5. Implement Single Sign-On (SSO)
SSO strengthens security while improving agent efficiency by centralizing authentication.

Benefits of SSO:
– Reduced password fatigue
– Centralized access control
– Improved security monitoring
– Faster account provisioning
– Enhanced compliance tracking
6. Maintain Detailed Audit Logs
Comprehensive audit logs are crucial for security monitoring and compliance.
Essential Logging Elements:
– User login attempts
– System configuration changes
– Data access and modifications
– Security-related events
– Administrative actions
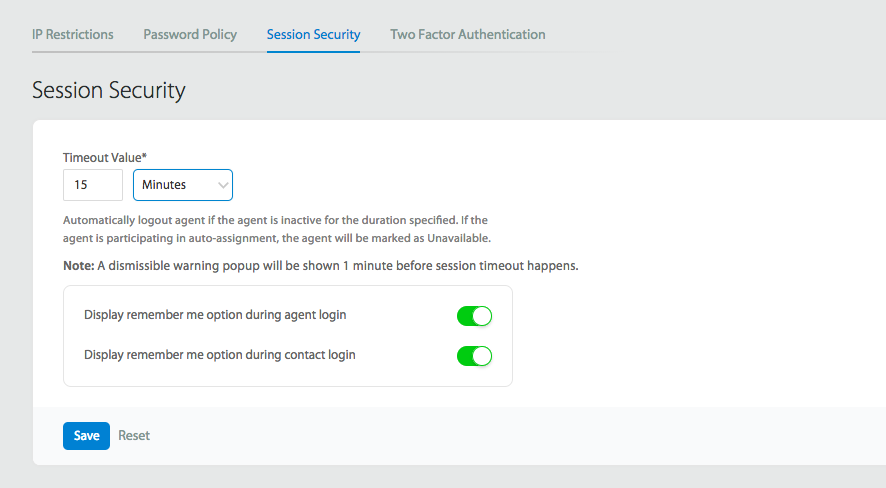
7. Set Custom Data Retention Rules
Smart data retention policies help minimize risk while meeting compliance requirements.
Key Considerations:
– Define retention periods by data type
– Implement automated deletion policies
– Ensure compliance with regulations
– Create data archiving procedures
– Document retention decisions
8. Ensure Compliance Standards
Meeting industry compliance standards isn’t just about checking boxes – it’s about protecting your customers.
Critical Compliance Areas:
– SOC 2 Type II standards
– CCPA regulations
– Industry-specific compliance
– International data protection laws
9. Regular Security Training
Your security is only as strong as your least-trained team member.
Training Program Elements:
– Social engineering awareness
– Password security best practices
– Data handling procedures
– Incident response protocols
– Security policy updates
10. Monitor and Respond to Security Events
Proactive security monitoring helps catch and address issues before they become breaches.
Essential Monitoring Activities:
– Real-time security alerts
– Access pattern analysis
– Suspicious activity detection
– Regular security assessments
– Incident response planning
How HappyFox Empowers Service Security
HappyFox’s enterprise-grade security framework provides comprehensive protection for your customer service operations through multiple layers of advanced security features:
Advanced Security Infrastructure
SOC 2 Type II Certification: Demonstrating our commitment to maintaining rigorous security controls and protecting customer data
GDPR Compliance: Full compliance with data protection regulations, ensuring proper handling of customer information
256-bit SSL Encryption: Enterprise-grade encryption protecting all data communications
Custom Data Retention Rules: Flexible data management to meet your compliance needs
IP Range Restrictions: Advanced controls to manage system access
Two-Factor Authentication: Additional security layer for user authentication
Access Control and Monitoring
Role-Based Access Control: Manage permissions effectively across your support team
Comprehensive Audit Logs: Track and monitor system activities
Single Sign-On (SSO): Streamlined, secure authentication process
Activity Monitoring: Keep track of system usage and security events
Custom Password Requirements: Account owners can set specific password policies including length and complexity requirements
Secure Your Customer Service with HappyFox
In today’s threat landscape, robust customer service security isn’t optional – it’s essential for business survival. HappyFox provides the enterprise-grade security features you need to protect customer data, maintain compliance, and build trust.
Ready to strengthen your customer service security? Schedule a demo with HappyFox today and discover how our advanced security framework can protect your customer service operations.